
[Avis d'expert] Gallo Fall : "Reconquérir la souveraineté numérique du Sénégal après la cyber-attaque du DAF"
Gallo Fall lives and works in the United States and believes that protecting Africa's digital ecosystem and its future is imperative. He has held several leadership positions in cybersecurity. He earned a BS in Computer Science and Network Security with a minor in Computer Forensics from Dakota State University, followed by an MS in Security Technologies from the University of Minnesota, specializing in cybersecurity, critical infrastructure, and risk management.
This article highlights the symbolic weight of biometric and identity systems while underscoring the long-term risks associated with the compromise of national biometric data. This editorial emphasizes the importance of digital sovereignty and urges Senegal and other African nations to take control of their digital future by building secure and resilient systems to host and protect what matters most in terms of cybersecurity.
The recent cyberattack against the Directorate of File Automation (DAF) has revealed a critical vulnerability at the heart of our Republic. According to publicly available information, a group calling itself "The Green Blood Group" claims to have exfiltrated 139 terabytes of highly sensitive data, thereby disrupting the issuance of national identity cards and passports and potentially compromising the biometric and administrative information of millions of Senegalese citizens.
I am writing to you as a cybersecurity and risk governance expert to urge you to provide a decisive response that goes beyond technical solutions and addresses the fundamental problem: Senegal's digital sovereignty.
To explain the amount of data stolen from non-specialists, it's important to clarify that storage capacity is generally measured according to two different standards: decimal (SI), used by hardware manufacturers, and binary (IEC), often used by operating systems. MB stands for megabytes.
1 gigabyte (GB) = 1000 megabytes, according to the decimal standard, or 1024 megabytes according to the binary standard (IEC). 1 terabyte of storage can hold approximately 250,000 to 300,000 photos (assuming 12-megabyte photos).
A storage capacity of 139 terabytes allows you to store approximately 11,583,333 photos of 12 megabytes each using standard decimal conversion, or 12,146,005 photos using binary conversion.
Who is Green Blood Group?
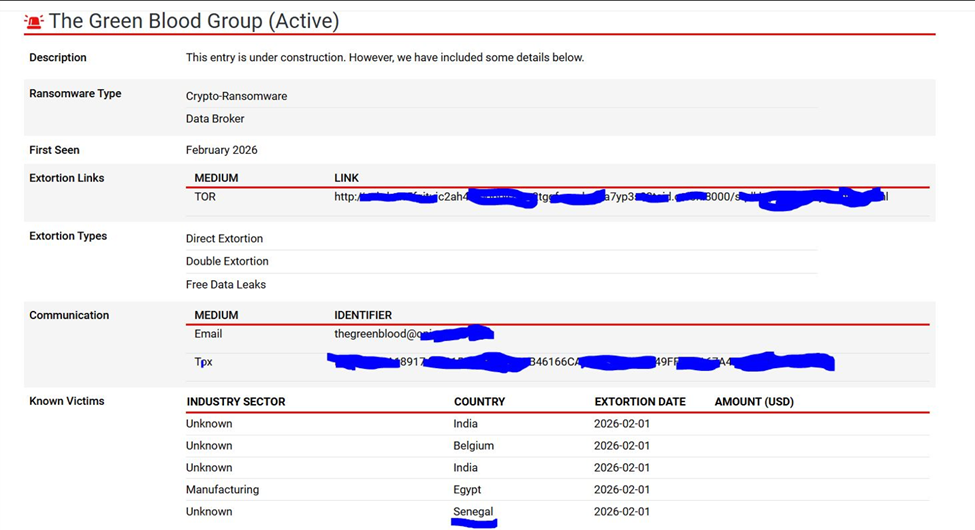
Green Blood Group is a ransomware-driven cybercriminal group first observed in February 2026. According to available information, it belongs to the ransomware ecosystem, which combines data theft and extortion. Their activities follow the general trend of small, agile groups using readily available tools, anonymous communication channels, and public leak sites to coerce victims into paying. The group operates a dedicated leak site on the Tor network and employs a double extortion model, threatening to publicly release victims' data if negotiations fail.
The Green Blood group appears to be a new ransomware organization, not simply a reorganization of an existing one. This group operates an independent data leak site on the Tor network and uses encrypted communication channels to interact with its victims.
Types of extortion:
• Direct extortion
• Double extortion
• Free data leaks
Target countries observed
The targeting method suggests a focus on regions where incident response maturity and ransomware attack disclosure requirements vary, which could increase the likelihood of successful extortion attempts.
• Senegal
• India
• Colombia
• Egypt
• Belgium
The danger of outsourcing identity
The cyberattack occurred precisely when the Senegalese government was embroiled in a commercial dispute with IRIS Corporation Berhad, the Malaysian company responsible for Senegal's digital national identity cards. Upon detecting the intrusion, IRIS reportedly instructed the DAF (Directorate of File Automation) to deactivate all systems, while its technical team prepared to travel to Senegal from Malaysia. In other words, in the midst of a national emergency, the operation and restoration of Senegal's critical identification infrastructure depended entirely on a foreign supplier located thousands of kilometers away. This is not simply a complication related to public procurement, but a profound strategic vulnerability: when the continuity of our national identification system relies on an external provider involved in a financial dispute with the state, a portion of our sovereignty is already compromised. The convergence of a major cyberattack, a trade dispute, and a demand to take national systems offline reveals a structural weakness that investigators must examine closely, including the possibility that the relationship with the supplier itself created or amplified the security vulnerabilities currently being exploited.
This arrangement raises three serious concerns:
Furthermore, publicly available information suggests that other strategic entities, including Sénégal Numérique S.A. ( SENUM SA) , the state-owned company responsible for government digital infrastructure, were also targeted, indicating a broader campaign against our institutional “digital vaults.” Combined with previous attacks against the Directorate General of Taxes and State Property, these actions reveal a pattern of systemic vulnerability at the highest level of the state’s information systems.
Data sovereignty as a constitutional imperative
Data sovereignty is the contemporary form of state sovereignty in the digital age. It is not a technical slogan; it is a constitutional imperative that must guide the acquisition, architecture, and governance of all critical information systems.
The Constitution affirms the sovereignty of the Senegalese people over their territory and institutions. However, in the digital age, this sovereignty must also extend to data and digital infrastructure. Biometric databases, civil registers, tax records, immigration files, and electoral lists constitute the informational backbone of the Republic, determining legal identity, access to rights, tax obligations, and democratic participation.
If these digital vaults can be opened, encrypted or taken hostage by criminal groups – or indirectly influenced by foreign entities that run the systems – then our sovereignty exists only on paper.
The DAF incident, combined with previous attacks against institutions such as the Directorate General of Taxes and State Property and reports that SENUM SA, the state-owned company responsible for protecting government data, was also compromised, reveals a pattern of systematic exploitation of high-level vulnerabilities. These breaches are not isolated incidents; they are symptoms of an architecture that has prioritized speed and outsourcing over national control and resilience.
A political program for digital independence
In light of the above, I respectfully propose that the government consider the following measures, building on existing strategies but strengthening them in terms of scope and urgency:
1. Enshrine sovereignty and data localization for critical systems. Define, by law or decree, categories of “critical national data” (including biometric, tax, health, electoral, and security data) that must be stored and processed on infrastructure physically located in Senegal and operated under direct national control. Require that any foreign partnership involving such data include clear provisions for state access to source code, cryptographic keys, and operational documentation, without granting external providers unilateral power to disable or suspend the systems.
2. Rebalance contracts in favor of national capacity: Review the contract with IRIS Corporation and similar arrangements to ensure they do not create strategic dependency or limit the State's ability to operate and secure its own systems. For future tenders, mandate technology transfer, joint ventures with Senegalese companies, and capacity-building clauses requiring foreign partners to train and integrate national teams in the design, operation, and defense of these systems.
3. Strengthen national cybersecurity governance and enforcement. Empower a central national cybersecurity authority with a clear mandate to audit, certify, and monitor all critical systems, whether operated by public agencies or private contractors. Require regular and independent security assessments, penetration tests, and incident response exercises, with comprehensive reporting to the relevant parliamentary committee to ensure democratic oversight.
4. Invest in Senegalese cybersecurity talent and industry. Create dedicated funding mechanisms for training cybersecurity engineers, digital forensics specialists, and security architects through partnerships between government, universities, and the private sector. Encourage the growth of local cybersecurity companies capable of competing for government contracts, thereby preserving expertise and economic value in Senegal and the wider ECOWAS region.
5. Promote transparency and public trust after the breach. Publish, as soon as possible without compromising security, an official and technically sound report on the DAF incident, detailing the extent of the affected data, the actions taken, and the planned reforms. Establish clear communication channels with citizens whose data may have been exposed, and develop remediation programs (such as enhanced monitoring, document renewal, and support services) to mitigate potential risks.
A broader African warning
Senegal’s experience resonates with a broader African reality. From national identity contracts and immigration systems to smart city platforms, many African states have turned to external providers for turnkey digital infrastructure. While these arrangements can accelerate modernization, they often create opaque dependencies and expose fundamental public systems to both cybercriminal and geopolitical risks. Countries that have begun to internalize cybersecurity capabilities and exercise greater control over their data—such as those that are creating national cybersecurity agencies and investing heavily in domestic digital industries—demonstrate that another path is possible.
Africa cannot afford a future where the identities of our citizens, electoral registers, and state archives are effectively at the mercy of external actors, whether dark web hackers or vendors in distant capitals. The breach of the DAF should therefore be investigated not only in Dakar, but in every capital city where biometric and identity systems are acquired or renewed.
From the alarm bell to the plan
The government's immediate priority is rightly to contain the DAF incident: restoring services, assessing the full extent of the data breach, and cooperating with investigators to identify and prosecute those responsible. But once the immediate crisis is over, Senegal must resist the temptation to "return to normal," because it is precisely this return to normalcy that made this crisis possible.
On the contrary, this vulnerability should serve as a model for a national digital sovereignty program—a program that puts Senegalese citizens, institutions, and experts at the heart of our identity infrastructure. If we see this moment as a turning point rather than an embarrassment to be buried, Senegal can emerge as a continental leader in responsible and sovereign digital governance.
The Sang Vert group may have revealed our weaknesses, but it also clarified our path. The question now is whether we will follow it.
Turning the crisis into an opportunity
Senegal has an opportunity to transform this serious incident into a catalyst for positive structural change. By asserting digital sovereignty, developing strong national capabilities, and rebalancing its partnerships, the country can emerge as a regional leader in secure and accountable digital governance. In a context where many African states are grappling with similar questions regarding foreign-managed identity systems and large-scale data breaches, Senegal's response will send a powerful signal across the continent.
I am convinced that Senegal possesses the human capital, institutional maturity, and diplomatic standing necessary to chart this course. What is needed now is a clear political decision: to treat digital infrastructure and cybersecurity not as secondary technical issues, but as fundamental elements of national security and sovereignty.
I am available to help Senegal secure what matters most and improve its cybersecurity risk management posture.
If you have any questions or would like a follow-up, please email me at fallgallo@gmail.com .
Respectfully,
Commentaires (2)
Participer à la Discussion
Règles de la communauté :
💡 Astuce : Utilisez des emojis depuis votre téléphone ou le module emoji ci-dessous. Cliquez sur GIF pour ajouter un GIF animé. Collez un lien X/Twitter ou TikTok pour l'afficher automatiquement.